These functions are delivered from the cloud and provided as a service by the SASE vendor. ARCON Privileged Access Management PAM allows enterprise security teams to secure and manage the entire lifecycle of their privileged accounts.
 Security Services Identity Access Management Service Provider From Panaji
Security Services Identity Access Management Service Provider From Panaji
Information technology IT system that gives authorized personnel secure access to non-public CDC applications.

Secure access management. Identity and Access Management IAM Microsoft Security Secure access for a connected world Protect your organization with Azure Active Directory Azure AD a complete identity and access management solution with integrated security that connects 425 Million people to their apps devices and data each month. Secure Access Your Way Ensure every access request to your valuable resources is evaluated by the industrys most advanced risk check engine. Secure Identity and Access Management Identity management is the discipline of helping in the effective management of the users access rights.
Access management features such as authentication authorization trust. Smart modern identity solutions deliver a frictionless and secure experience for every user asset and data interaction providing a foundation for a zero trust strategy. Through our advanced Secure Identity and Access Management services we offer our extensive expertise in integrating and architecting the enterprise-oriented solutions.
Its a tool well-suited to both documenting and enforcing security requirements. If you are still reliant upon manual processes you could be exposing your organisation to a potentially damaging breach. Identity and access management IAM is a framework of business processes policies and technologies that facilitates the management of electronic or digital identities.
Identity and access management IAM is essential for securing the hybrid multicloud enterprise. Using Cyral for automated access management in this manner has the following benefits. Visibility on your systems and solutions is the first step in any process to successfully manage and secure assets.
Secure Access Management Services SAMS Registration The Centers for Disease Control and Preventions CDC Secure Access Management Services SAMS is a federal. IBM Security Verify Access formerly IBM Security Access Manager or ISAM helps you simplify your users access while more securely adopting web mobile IoT and cloud technologies. This warning banner provides privacy and security notices consistent with applicable federal laws directives and other federal guidance for accessing this Government system which includes all devicesstorage media attached to this system.
Open Policy Agent OPA is an open-sourced policy engine that enables unified context-aware policy enforcement across an entire stack. SecureAuth delivers a friction free user experience with industry leading security options to protect. Unauthorized or improper use of this system is prohibited and may result in.
Secure access service edge SASE is a network architecture that combines VPN and SD-WAN capabilities with cloud-native security functions such as secure web gateways cloud access security brokers firewalls and zero-trust network access. Asset Discovery and Management. This system is provided for Government-authorized use only.
It can be deployed on-premises in a virtual or hardware appliance or containerized with Docker. LTS Secure Access Management built from the latest next generation technologies provides the most comprehensive and flexible set of services required for consumer facing access management as well as traditional access management capabilitiesThese services include authentication mobile authentication adaptive risk assessment authorization federation single sign-on social sign-on basic self service. Modern access management solutions require a delicate balance between security and user experience to deliver successful outcomes for healthcare organizations.
Ad Free membership to the largest CRM networking group in the call center industry. Access management refers to the processes and technologies used to control and monitor network access. It protects privileged credentials from the exploits of compromised insider attacks and third-party cybercrime.
Customize access security and be confident that only authorized users are granted access. Security policies can be dynamically enforced through the access management layer eliminating the need to restart infrastructure. Administrators can implement strong security hygiene by eliminating shared account access to databases and getting rid of provisioning and deprovisioning of individual accounts.
Hybrid access management to protect every user and app. With an IAM framework in place information technology IT managers can control user access to critical information within their organizations. Learn more about Azure AD.
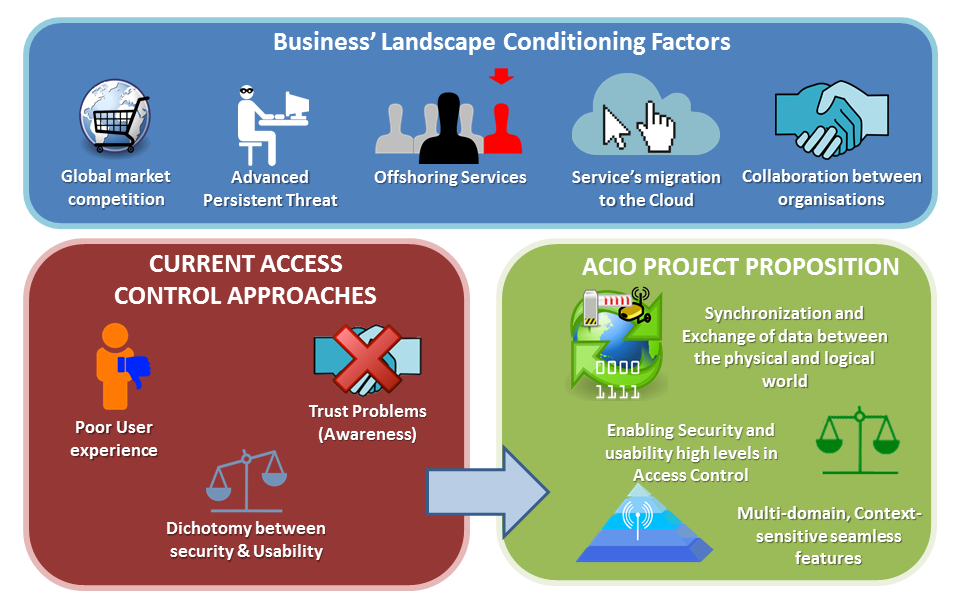 Simplified Access Control For Sea Ports Celtic Plus Project Acio Celtic Next
Simplified Access Control For Sea Ports Celtic Plus Project Acio Celtic Next
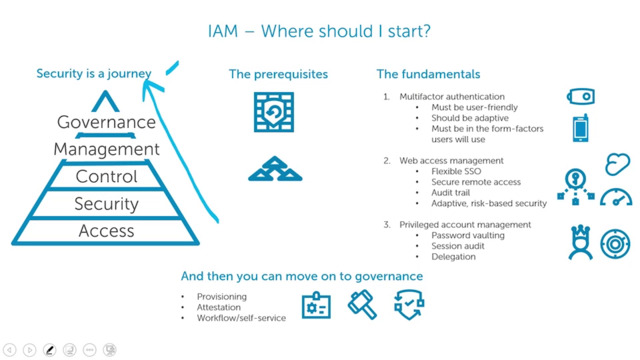 Learn Where To Start With Identity And Access Management
Learn Where To Start With Identity And Access Management

 Blockchain Secure Identity Access Management
Blockchain Secure Identity Access Management
 What Is Access Control A Key Component Of Data Security Cso Online
What Is Access Control A Key Component Of Data Security Cso Online
Secure Access To Enterprise Information With Identity Access Management
Network Security Secure Access And Identity Access Management Lanworks
 Usam Universal Secure Access Management Silverlake Sheaf
Usam Universal Secure Access Management Silverlake Sheaf
 Access Management What Is It And How To Manage Monitor In 2021
Access Management What Is It And How To Manage Monitor In 2021
 Access Management And Access Control In The Security Layer Download Scientific Diagram
Access Management And Access Control In The Security Layer Download Scientific Diagram
 Secure Identity And Access Management Secure Networks
Secure Identity And Access Management Secure Networks
 What Is The Importance Of Secure Access Management Check Here Encieza Digital
What Is The Importance Of Secure Access Management Check Here Encieza Digital
 Data Cloud Security Secure Access Management White Paper
Data Cloud Security Secure Access Management White Paper
 Devops Case Of Making Secure Access Management Services
Devops Case Of Making Secure Access Management Services
Tidak ada komentar:
Posting Komentar
Catatan: Hanya anggota dari blog ini yang dapat mengirim komentar.